Advertisement
Have you ever had the need to send anonymous emails to someone? Maybe you’re discreetly declaring your love to someone. Or maybe you’re a journalist and need to secretly communicate with an informant.
There are plenty of legitimate reasons someone may want to send anonymous email. There are free online services on the web that allow you to do this. Or you can use a VPN and an anonymous burner email account (i.e. throwaway).
These days it’s very easy to send emails without having to reveal your true identity. In this article, you’ll learn how to send an anonymous email using the five most effective methods we’ve found.
1. Burner Email Account + VPN
Using a web-based email account like Gmail is a great option. You can sign up for a Gmail account without providing any actual identifying information, and then use that address as a kind of burner email account.
When you send anonymous emails from Gmail’s web-based email client, the originating IP in the SMTP envelope is Google’s server, not your own computer’s IP. This is a nifty way to hide your IP address from the receiver
How to Use a Fake IP Address & Mask Yourself Online
How to Use a Fake IP Address & Mask Yourself Online
Sometimes you need to hide your IP address. Online anonymity continues to be important as privacy gets trampled. Here are some ways to cloak your I.P address and mask yourself online.
Read More
.
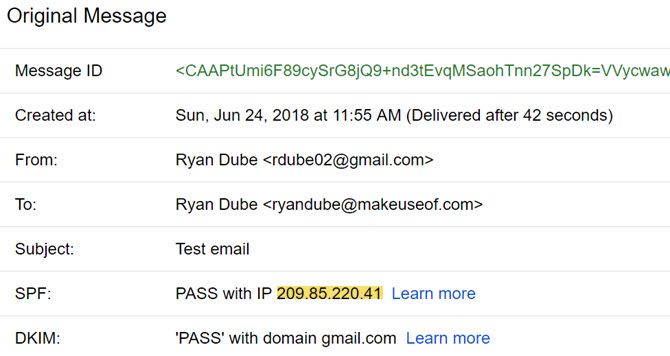
If someone were to trace the IP that show up when you send an email from the online Gmail account, it would only trace to the nearest Google server to you. Which, in my case, is the Wichita, Kansas area.
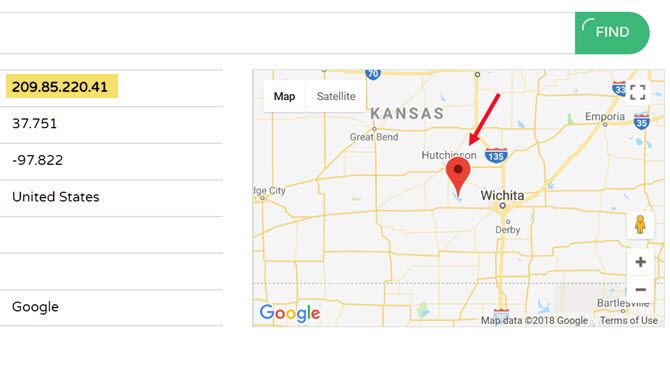
With that said, your actual IP address is stored on Google’s systems. So, if the government or any other authority ever came knocking and asked for your location, Google could provide it.
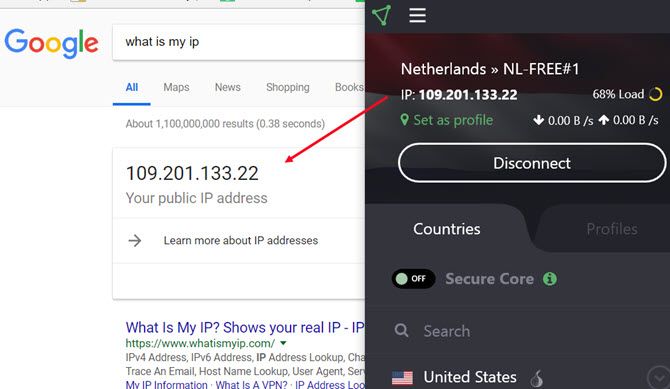
If that’s not enough privacy for you, you can add another layer of anonymity by encrypting your connection with a VPN service. We recommend avoiding free VPN services and instead pay for a reputable one like ExpressVPN or CyberGhost.
Once connected, you can then use Gmail through the encrypted VPN.
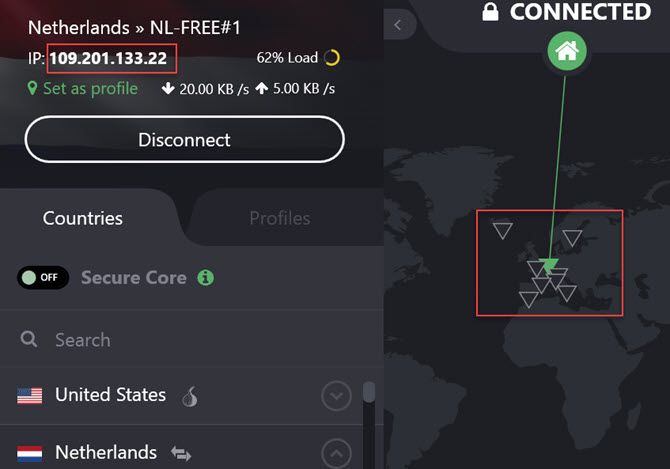
Now, when you go to your Gmail account and send an email, the originating IP will still show up as one of Google’s servers, but there will be two differences.
First, the Google server won’t likely be located anywhere near your actual location. Second, if Google is ever asked to provide your actual IP, they’ll only be able to provide the erroneous IP address hosted by the VPN service.
Note: An anonymous burner email account isn’t quite the same as a disposable email account
Need a Disposable Email Address? Try These Great Services
Need a Disposable Email Address? Try These Great Services
Need to send or receive an email without using your real address? Here are some great services that let you do just that.
Read More
!
2. Email Client + VPN
Another solution that avoids the need for any anonymous email service is using an email client like Thunderbird on your own PC.
There are three steps you’ll need to follow to make this approach work:
All you have to do is fire up your preferred VPN service and make sure your computer has a remote IP address.
Then, just send an email via your throwaway email account using your desktop email client, just like you normally would.
The difference is that now, instead of the header providing your actual originating IP address
What Can You Learn From An Email Header (Metadata)?
What Can You Learn From An Email Header (Metadata)?
Did you ever get an e-mail and really wondered where it came from? Who sent it? How could they have known who you are? Surprisingly a lot of that information can be from from the…
Read More
, it’ll show your VPN’s IP address located some place far away. It’s a quick and easy way to send anonymous emails with very little effort.
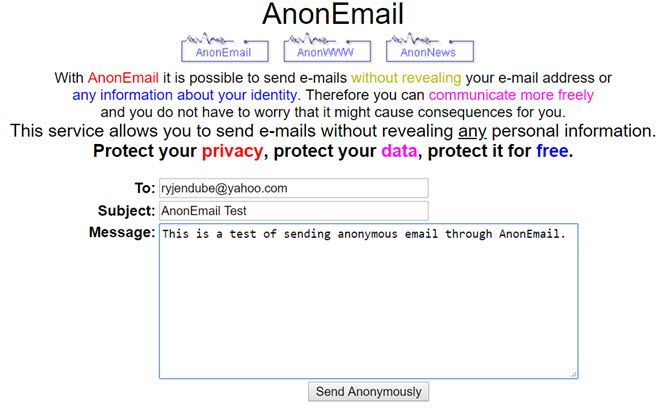
AnonEmail is a service by AnonyMouse. It allows you to send anonymous emails by resending your email several times through random nodes, thus making it impossible to trace back.
In AnonEmail, you can fill in your recipient, the subject, and a short plain-text message. Contrary to many other services AnonEmail does not (seem to) log your IP. However, we urge you not to use it for anything illegal!
As an extra security measure, AnonEmail will wait for an unknown period of time before sending your email along. Why? So no one will be able to prove your “guilt” based on time/location, or make geographic presumptions based on timezones.
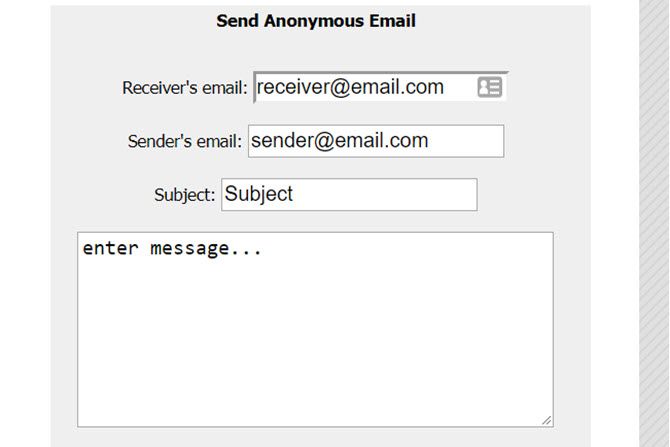
Like the name implies, this is another web-based, anonymous email tool. Although it lacks the complete anonymity of AnonEmail, it’s the simplest option to use.
You’ll be able to specify a sender’s address and a fake origin email address for your secret message. This one logs your IP address, so you’ll need to use a free VPN service
7 Completely Free VPN Services to Protect Your Privacy
7 Completely Free VPN Services to Protect Your Privacy
If you’re looking for a free VPN, the choices are currently limited, with many services switching to a paid model. These free virtual private networks can be used to avoid region blocking and more.
Read More
if you want to fully cover your tracks.
Also, neither Send Anonymous Mail nor AnonEmail allow the recipient to reply to your email, so these solutions are only best if you want to send a one-way anonymous email message.
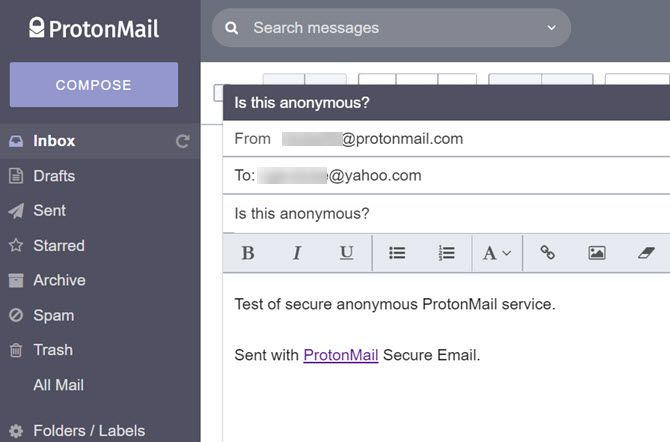
If you absolutely need secure, anonymous, two-way email conversation, ProtonMail is a popular solution. Many say that ProtonMail is better than Gmail
Gmail vs. ProtonMail: Which Email Client Is Best for You?
Gmail vs. ProtonMail: Which Email Client Is Best for You?
While Gmail may be the most convenient email client, ProtonMail is more secure. Which one is right for you? We’ll help you find out with this comparison.
Read More
.
I’ve personally used ProtonMail when communicating with a journalist living in China. The journalist was using a VPN to access his ProtonMail account, providing several levels of security from prying government eyes. Not only was his originating IP address located outside of China, but all communications using ProtonMail are encrypted.
Some features of ProtonMail include:
- End-to-End Encryption: Messages are not only encrypted when they’re sent from ProtonMail servers, but all stored messages are encrypted as well. Without access to the appropriate ProtonMail account, no one can access your messages.
- Private User Data: ProtonMail’s encryption process, which uses an encryption key on your own client computer, mean even the system administrators at ProtonMail can’t access your messages. On the downside, this means they can’t recover your account for you. On the upside, it means they can’t provide messages to any governing authority either.
- Open Source Cryptography: Since ProtonMail uses open-source cryptographic libraries
5 Common Encryption Types and Why You Shouldn’t Make Your Own
5 Common Encryption Types and Why You Shouldn’t Make Your Own
Is it a good idea roll your own encryption algorithm? Ever wonder what types of encryption are the most common? Let’s find out.
Read More
, you can be sure there are no “back doors” available for anyone to access your emails. That includes both system administrators or hackers.
If you have a need for regular two-way encrypted emails, you may want to consider signing up for a ProtonMail account and just using it as your regular email service.
Start Sending Anonymous Emails Your Way
As you can see, there are a lot of ways to send anonymous email. You can use a local solution with a VPN and either an email client or through a throwaway online email account. You could use a secure, encrypted email service like ProtonMail. Or you could just use one of the free websites that let you send one-way, fully-anonymous messages.
The choice really depends on why you’re sending the message and what level of security and anonymity you need.
Not sure which VPN service is right for you? See our comparison of the best VPN services
The Best VPN Services
The Best VPN Services
We’ve compiled a list of what we consider to be the best Virtual Private Network (VPN) service providers, grouped by premium, free, and torrent-friendly.
Read More
. If you’re looking for other ways to bolster your personal security, you may also want to take a look at boosting your PC’s security
The Best Computer Security and Antivirus Tools
The Best Computer Security and Antivirus Tools
Need a security solution for your PC? Concerned about malware, ransomware, viruses, and intruders through your firewalls? Want to back up vital data? Just confused about it all? Here’s everything you need to know.
Read More
.
via MakeUseOf.com
How to Send Completely Anonymous Emails: 5 Effective Methods



 Troubleshooting crashes is never a fun task, especially if MySQL does not report the cause of the crash. For example, when MySQL runs out of memory. Peter Zaitsev wrote a blog post in 2012:
Troubleshooting crashes is never a fun task, especially if MySQL does not report the cause of the crash. For example, when MySQL runs out of memory. Peter Zaitsev wrote a blog post in 2012: 
