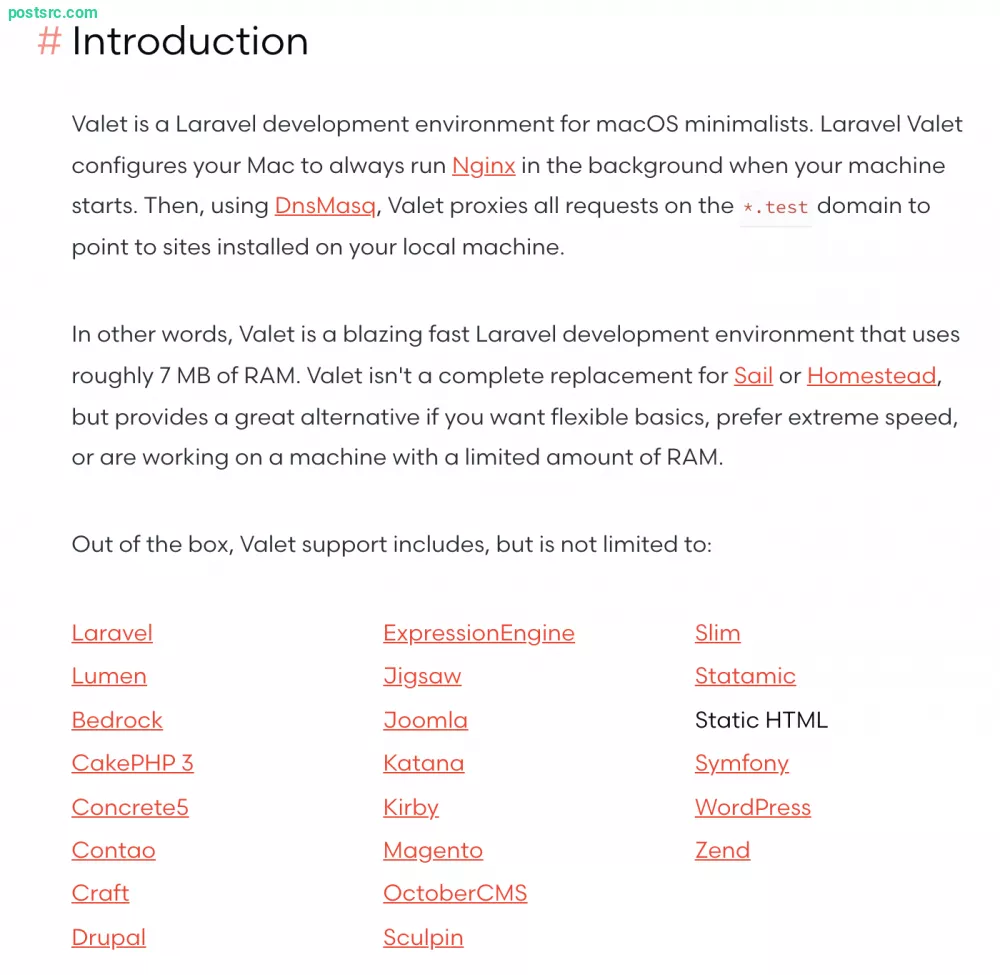
https://www.futurity.org/wp/wp-content/uploads/2022/01/feet-covid-19-working-from-home-slippers-1600.jpg
If you’ve been spending more time at home during the pandemic, you may not realize how important proper footwear is for keeping certain injuries at bay.
Sean Peden, an orthopaedic foot and ankle specialist from Yale University Medicine, says not wearing supportive footwear on a regular basis can lead to foot pain and other problems.
“Many people are continuing to work at home part- or full-time, which for some can mean wearing slippers or walking around barefoot,” Peden says. “And because of that, many patients are coming to us with foot problems.”
Taking good care of your feet will not only help you avoid common injuries like tendonitis and plantar fasciitis, but it can also prevent other issues with your hips, knees, and back from developing, he adds.
Here, Peden shares some of the most common foot problems he sees—and simple treatments to get relief:
Think of shoes as shock absorbers
Just as you would pick out an appropriate shoe for your commute into the office, it’s important to put the same level of thought into selecting an at-home shoe.
Walking barefoot at home is not recommended for the same reason walking barefoot outside is ill-advised, Peden says.
“All kinds of footwear protect your feet. Over the course of weeks or months, the strain of walking barefoot can add significant stress to your arches, tendons, plantar fascia, and joints,” he says. “This can lead to a range of complications, from minor conditions such as calluses to major issues such as arch collapse.”
It may help to think of footwear as shock absorbers and, based on body type and gait, some of us need more shock absorption than others, Peden says.
“If you have sore feet—or have had foot problems in the past—wearing a pair of what I call ‘house shoes,’ or ‘house slippers,’ is a good idea.”
By that, Peden means a hard-soled, slip-on shoe or slipper that is worn exclusively inside the home (ideally) to avoid bringing in dirt or bacteria.
“To be practical, I suggest a slip-on clog or slipper without laces. That way, you don’t have to tie and untie your shoes 10 times a day,” Peden says. “A hard sole is important because the harder the sole, the less stress the joints and tendons in your foot experience with each step. The hard sole transfers that stress to the shoe rather than to the foot.”
In general, avoid fluffy, formless slippers, he advises. “If you are at home, you might go up and down stairs dozens of times a day—or do chores around the house. And those are not activities to do with footwear that doesn’t have any support,” Peden says. “A good rule of thumb is if it isn’t something you could walk in for a few blocks comfortably, you shouldn’t wear it around the house all day, either.”
Painful tendonitis
One of the most common foot problems Peden has seen in patients since the pandemic started is Achilles tendonitis, or inflammation of a tendon (a thick cord of tissue that connects muscles to bones). The Achilles tendon runs from the back of your calf to your heel bone. Achilles tendonitis can cause pain and swelling in the foot and ankle.
An injury, overuse, and flat fleet are all causes for Achilles tendonitis, Peden says. “It can be an issue especially if people with flat feet spend six months to a year not wearing supportive shoes on a regular basis,” he says. “The tendon in the arch of the foot becomes inflamed as the foot gets flatter. It is quite painful and can be debilitating.”
Peden says he is also seeing more patients with posterior tibial tendonitis, which causes a collapsed arch or flat foot.
The Fix: For acute pain, the first things to try are rest, ice, and staying off your feet as much as possible. Finding footwear with good arch support is another must, Peden says.
“Some people might need an ankle brace or additional inserts for their shoes, but for the vast majority, proper footwear is the answer. These tendon flares generally last a few months, but patients usually see improvement within a week or two.”
People with tendon issues should get proper treatment, Peden says. “You want to avoid developing a chronic tendon issue, because those are harder to cure.”
Plantar fasciitis: ‘stabbing’ heal pain
Many patients have developed plantar fasciitis, inflammation of the band of tissue on the bottom of your foot.
A common symptom is a stabbing pain in the heel that can be the most intense when you first step out of bed in the morning. That’s because the plantar fascia, which runs from the heel to the base of your toes, tightens overnight.
The plantar fascia supports the arch of the foot and absorbs stress. Too much stress—from standing on your feet on a hard surface for a long time, improper shoes, or running—can cause irritation and tiny tears in the band of tissue.
“The pain is usually on the bottom part of the heel,” Peden says. “It’s associated with tight Achilles tendons and calf muscles. If people spend a lot of their day sitting, for example, the muscles can tighten up, and wearing improper footwear can exacerbate the issue.
“For people who work outside the home and are on their feet all day, including nurses, they should wear a supportive shoe—and not something too soft or flexible. This can include sneakers, a hard clog, or a work shoe, depending on personal preference.”
The Fix: Besides supportive footwear and avoiding walking around barefoot, treatment should include a home stretching program to address the tightness in the calf muscles and Achilles tendons, Peden says.
Another effective treatment is to wear a soft, flexible splint that holds your foot at a 90-degree angle while you are sleeping; this keeps the plantar fascia stretched out. You can also wear a splint while lying on the couch watching TV.
As painful as plantar fasciitis can be, Peden says it is not a progressive condition. “People often worry it’s the start of something like arthritis, which continues to get worse,” he says. “It might take a few months of conservative, noninvasive, nonsurgical treatments, but patients with plantar fasciitis typically get better.”
Physical therapy and lifestyle
Exercise, physical therapy, and weight loss can all make a difference in addressing foot pain, too.
“One pound of additional weight on your body leads to six pounds of additional pressure on your foot. So, if you lose 10 pounds, that is really taking 60 pounds of pressure off your foot,” Peden says.
With the pandemic, many people have gained weight, which compounds the problem. But the key is not to do too much too quickly to try to reverse it, Peden says.
“If you try to lose weight by suddenly walking too much, that’s hard on your feet, too, and may lead to other foot problems. So, I often recommend cross-training, including low-impact cardio activities like biking or swimming. You can walk, but try to take it easy and, as always, wear good, supportive shoes.”
Hiking shoes are often a good option, particularly if you walk on uneven surfaces, including trails. “They are a little safer than sneakers, and protect your foot and ankle better,” he says.
In certain cases, physical therapy is recommended for lingering foot issues. “Physical therapists have many techniques that can speed up the recovery process,” Peden says.
Surgery is rarely needed for chronic conditions like tendonitis or plantar fasciitis. “We always treat our patients first with nonsurgical options to hopefully manage the condition before we ever talk about surgery,” Peden says.
But if you are feeling foot pain, don’t be afraid to seek medical help, Peden advises.
“I know people have different comfort levels right now about seeking medical care during the pandemic, but if you have a foot issue and it’s been hurting for a while, you should go see your doctor. There are likely easy solutions.”
Source: Yale University
The post How to avoid achy feet while working at home appeared first on Futurity.
Futurity




 In this blog post, we will compare the performance of performing a backup from a MySQL database using
In this blog post, we will compare the performance of performing a backup from a MySQL database using 

