https://www.alloutdoor.com/wp-content/uploads/2023/10/atf-eforms-wait-times.png
Suppressors are awesome. They make shooting way more enjoyable. Sometimes, depending on the cartridge, you don’t even need ear pro. Suppressors can even improve accuracy and, where legal, they’re great for hunting. But unless the Hearing Protection Act – which would deregulate suppressors – is ever passed, you’ll have to go through some hoops to get your hands on a muzzle muffler. Here’s a quick n’ dirty guide on the steps you need to take to become the proud owner of a new suppressor. Of note, though: some states have simply banned the ownership of suppressors – the steps below cover the steps you need to take under federal law. You’ll also need to check if your state even allows for the ownership of suppressors, and whether there are extra steps you need to take.
Suppressor Coverage on AllOutdoor
- Catch Prey Off Guard with the New FN Catch 22 Ti Rimfire Suppressor
- Sub Guns and Suppressors: Is 9mm Better Than 300 Blackout?
- No More Dip? – Breakthrough Clean Technologies’ Suppressor Cleaner
- Suppressor Mounts: Direct Thread vs. Quick Attach
- Silencer Central Sponsors NWTF, Convention, and Sport Award Ceremony
“How Long Does the Suppressor Process Take?”
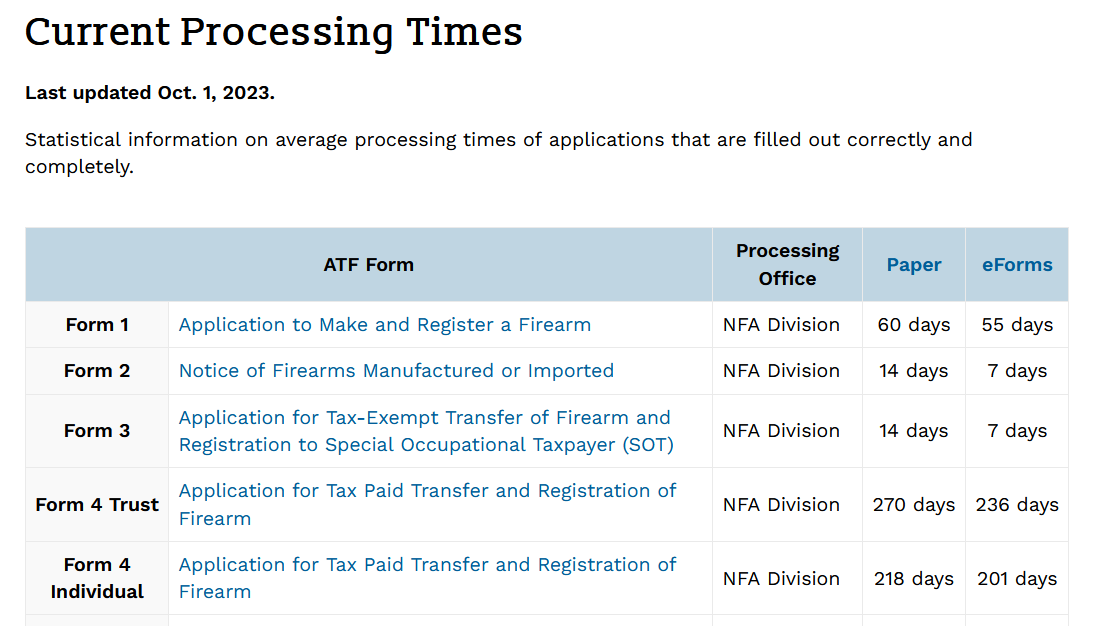
According to the ATF, the current lead time on processing the paperwork to buy a suppressor is about 270 days. That’s 38 weeks, or almost 10 months. Ouch. Indeed, buying a suppressor is a matter of patience. But, thankfully, the paperwork you need to fill out to own a suppressor is once-and-done. Once your application to buy a suppressor’s approved, you never need to renew any application, or pay any fees ever again (for that specific suppressor).
“Can I Do All the Suppressor Paperwork Online?”
Yes! And you definitely eForms should fill out your application to buy your suppressor online. Gone are the days of having to physically mail documents to some ATF field office – the feds have an online system that allows you to fill everything out on your phone or PC. It’s called , but we’ll talk about that more later.
“What’s a Gun Trust? Should I File as an Individual?”
There’s a lot of hot talk about using a gun trust to purchase an NFA item, especially suppressors. In truth, all a trust does is provide for easier transfer of ownership of your NFA items to a family member or designated beneficiary. There’s a matter of convenience, too. A gun trust allows any trustee to possess, transport, and use the NFA items within the trust at any point in time – with or without your physical presence.
Essentially, a trust allows multiple individuals to “stack on” to the application for your suppressor. Each trustee is considered an applicant, though – and that means they all have to provide personal information on your ATF application, including photos and fingerprints. Adding trustees and filing as a trust (instead of an individual) can also lead to delays if any one trustee’s background check or personal information gets caught up in any bureaucratic hurdles (like an incorrect social security number, a wrong home address, or your uncle’s old, unsightly DUI rearing its head).
To file as a trust, you have to actually make a trust, too. That means retaining an attorney to draft the paperwork, which costs extra. Personally, this writer always filed his ATF eForms applications as an individual. It’s quicker, more affordable, and less of a hassle trying to wrangle any would-be trustees to get me their requisite fingerprints, mugshots, and personal information. If you do want a gun trust, I highly recommend National Gun Trusts. They’re cheap – around $60 to $100 – and they’ve done thousands of trusts for gun owners, ensuring it’s quick and easy.
Step 1: Buy your Future Suppressor

Here’s the great news: You technically get to buy and “own” your suppressor before your application’s even approved. The only caveat is that you can’t actually take possession of it yet – your new can has to stay at the FFL you’re purchasing it from. But if your FFL happens to operate a shooting range, you can fire your new muzzle can all day long – or a rental that the FFL leases out for a fee. On that note, it’s a great idea to test out a few different models on your chosen firearm before you decide to purchase.
This is particularly important because once your application begins processing, you can’t back out: There is no option to change your chosen make or model, because the unique serial number of your suppressor is what ties your eForms application to the approval and ownership.
Step 2: Make an eForms Account
Once you’ve selected and paid for your suppressor, you’ll need to record the serial and register an account on the ATF’s eForms website. While registering, it’s important you accurately input your legal name and home address – it should match your home of record, not any business nor PO box. You can start filling out your application for your suppressor, but we recommend holding off until after step 3. You need to get your fingerprints ready, first. We’ll come back to the application process later.
Step 3: Roll your Fingerprints (Now Digital!)

Every eForms application for a suppressor requires a set of your fingerprints. This used to be a painful, mail-only process requiring the use of archaic FD-258 Fingerprint Cards. But now, you can get a digital set of fingerprints taken – and you can use that digital set for every eForms application you’ll ever submit!
To get digital prints for your eForms application, I recommend using PrintScan. They do digital printing for the FBI and various federal agencies, so they know what they’re doing. The cost is $45 (at the time of this publication). You can find a PrintScan location here, then schedule an appointment. After your appointment’s finished, simply download your prints from PrintScan, and then you’re ready to complete your eForms application.
Alternatively, you can also use the Silencer Shop Kiosk to get your fingerprints and other necessary affairs in order for your eForms application (more on that next). Just look for any “Powered By Silencer Shop” dealer in your area.
Step 4: Complete eForms “ATF Form 4”
ATF Form 4, “Application for Tax Paid Transfer and Registration of Firearm,” is the paperwork you must fill out on eForms. Many just call this a “form 4 application.” The process is pretty straightforward: Enter your personal information, the information pertaining to your suppressor – including the manufacturer, make, model, serial number, and caliber – and upload a picture of yourself, with your fingerprints.
The self-portrait is simple: Get someone to take a head-and-shoulders shot of you against a plain white background. You can even use your cellphone. Just make sure you’re not wearing glasses, jewelry, or any hats. If your photo looks like a passport or driver’s license portrait, you’re good to go.
Oh, you’ll also need to provide information about your local “chief law enforcement officer.” This is usually your local sheriff. You’ll want to record the name of the CLEO, and the address wherein he or she resides – usually the sheriff’s precinct. Have this info handy before filling out your application.
Step 5: Submit Application and Pay the $200 Tax
Once your application’s filled out, you’ll need to certify all the information contained therein is accurate, submit the application, and, sadly, pay our wonderful government $200 in the form of a tax. Yes, it’s dumb, but at least it’s a one-time fee. The eForms website accepts debit and credit card, which at least makes the humiliation a tad more convenient.
Step 6: Wait… and then Wait some more
Once you’ve submitted your Form 4 application, you’ll receive an email letting you know it’s in the pipeline for processing. At this point, comms will go dark for… quite a while. It’ possible your application could get approved more quickly than the advertised wait times, but expect to wait at least 8 to 9 months.
Step 7: Receive your Stamp, then Run to your FFL
Have faith, gunner: That fateful day will come. We’re talking about the day that you receive an email letting you know your ATF Form 4 application was approved, complete with your tax stamp showing you’re the proud, legal owner of a new suppressor. Print out your tax stamp and bring it to your FFL posthaste, so you can take ownership of your shiny (or matte) new muzzle muffler! There are loads of suppressor makers, and tons of models to pick from. Feeling overwhelmed? Start here, with our review of Dead Air’s new Mojave 9mm Suppressor.
The post So, You Want to Purchase a Suppressor?… Sweet! Here is How You Do It appeared first on AllOutdoor.com.
AllOutdoor.com














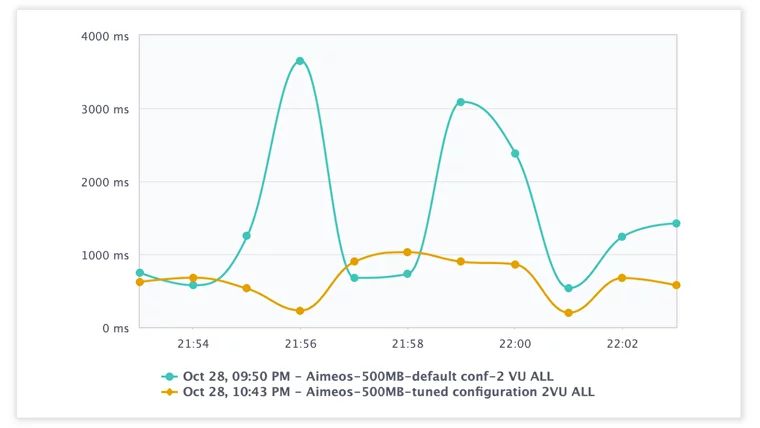 Response Time (ms), Aimeos Tuned MySQL Configuration vs Default
Response Time (ms), Aimeos Tuned MySQL Configuration vs Default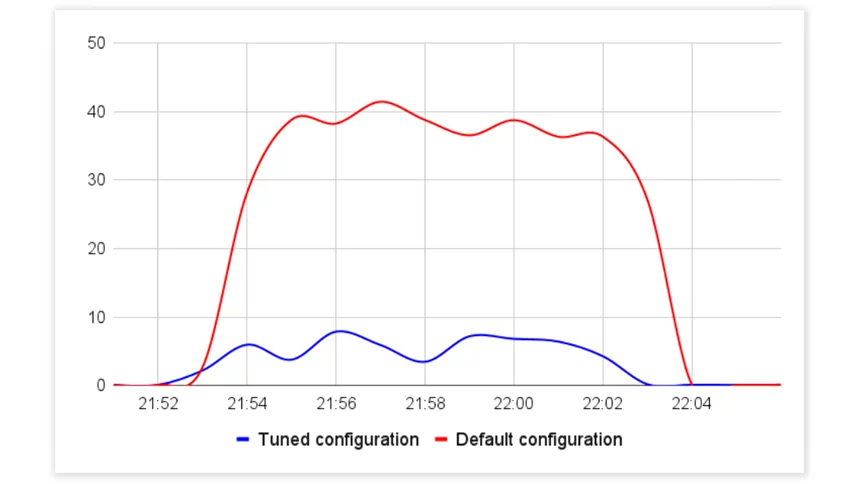 CPU Utilization (%), Aimeos Tuned MySQL Configuration vs Default
CPU Utilization (%), Aimeos Tuned MySQL Configuration vs Default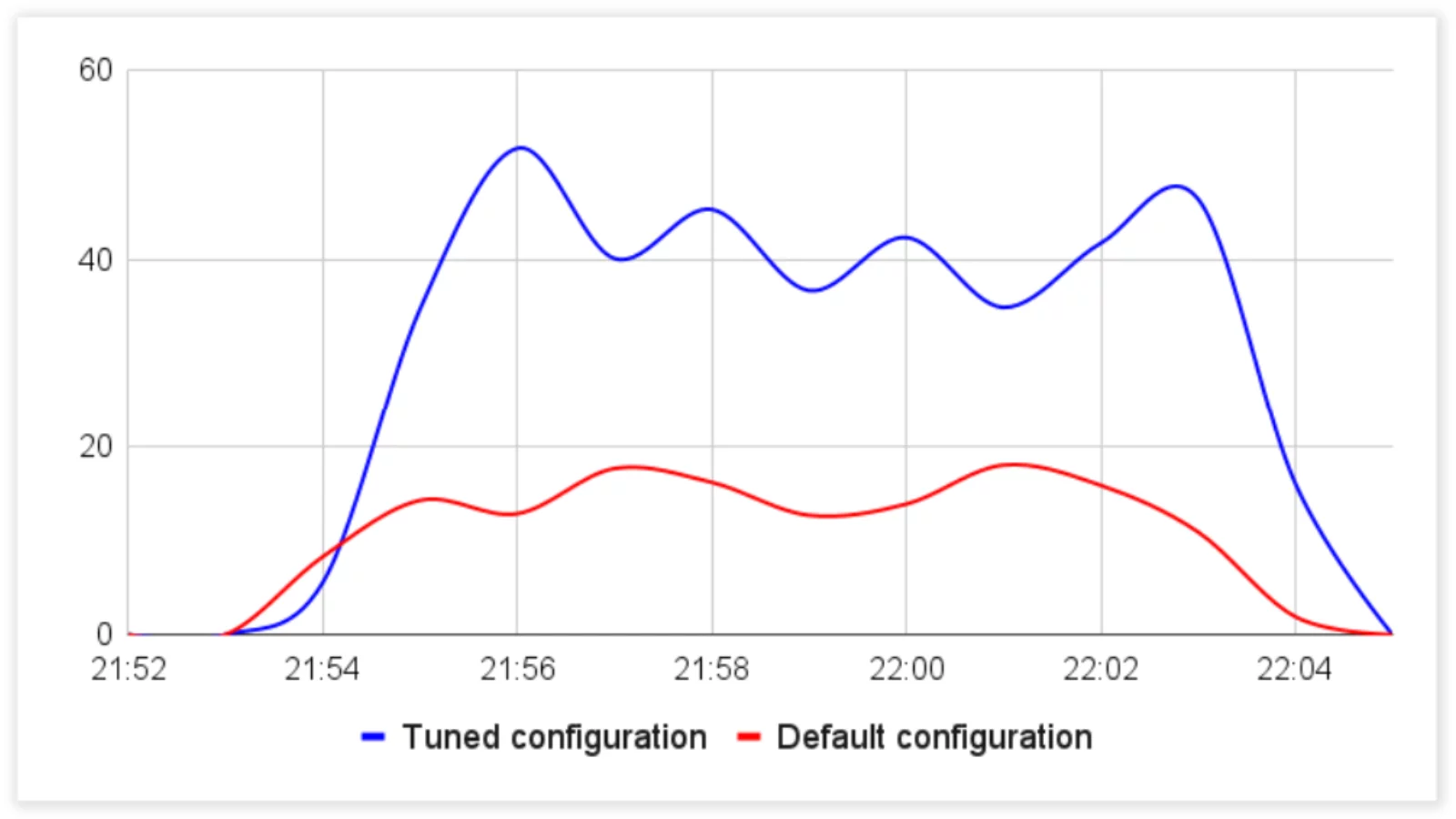 Queries Per Seconds, Aimeos Tuned MySQL Configuration vs Default
Queries Per Seconds, Aimeos Tuned MySQL Configuration vs Default