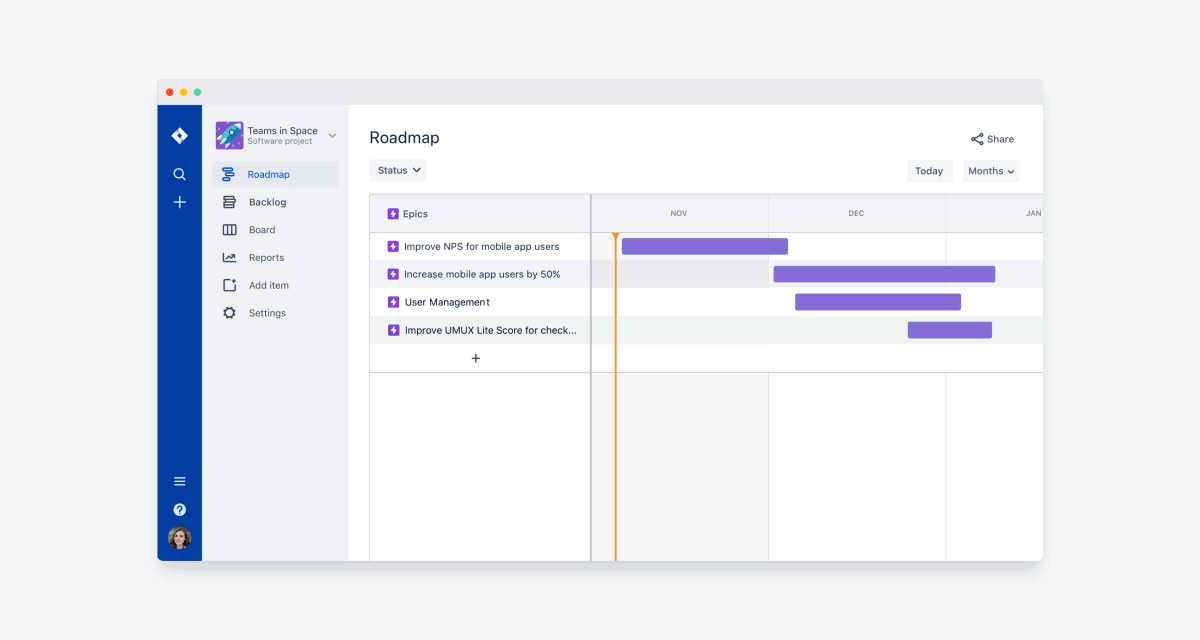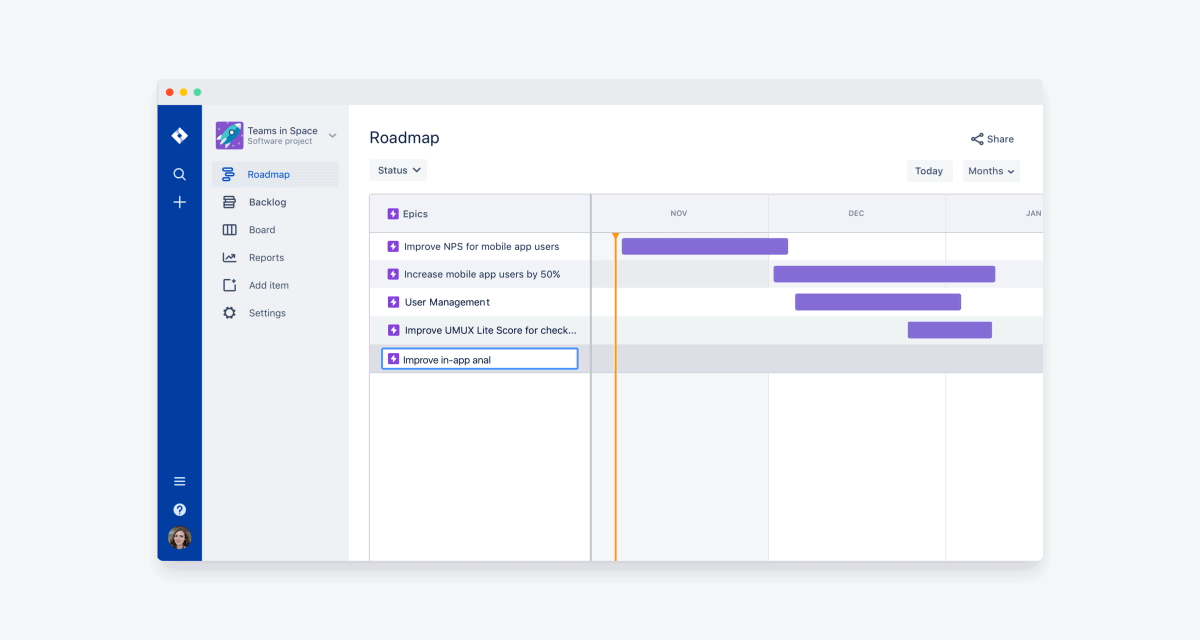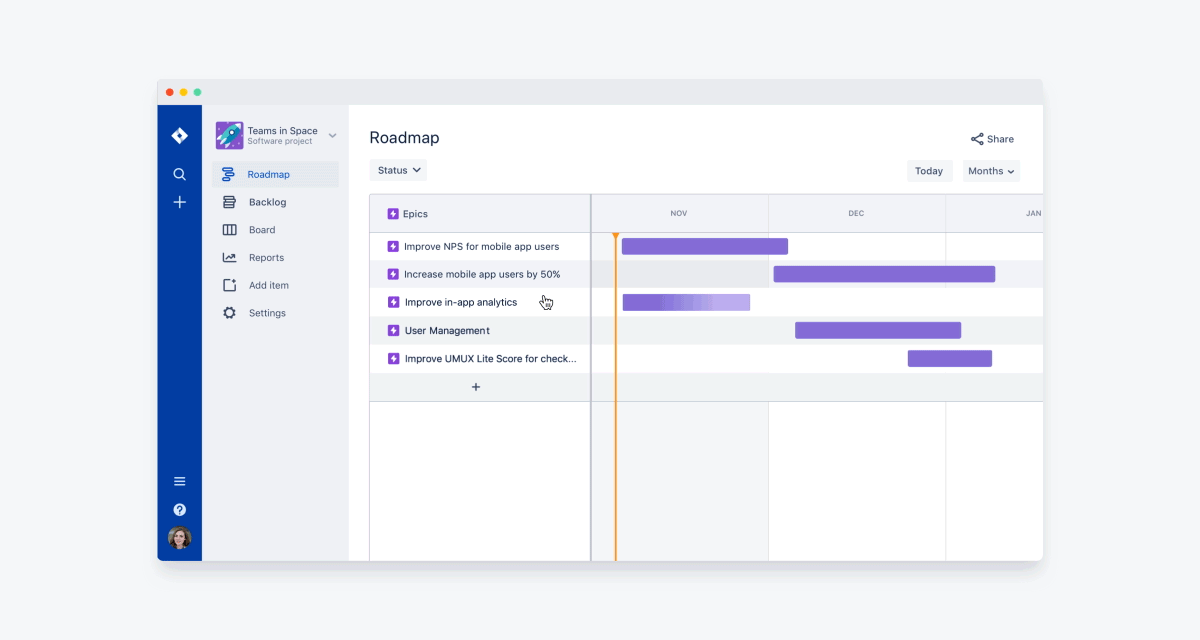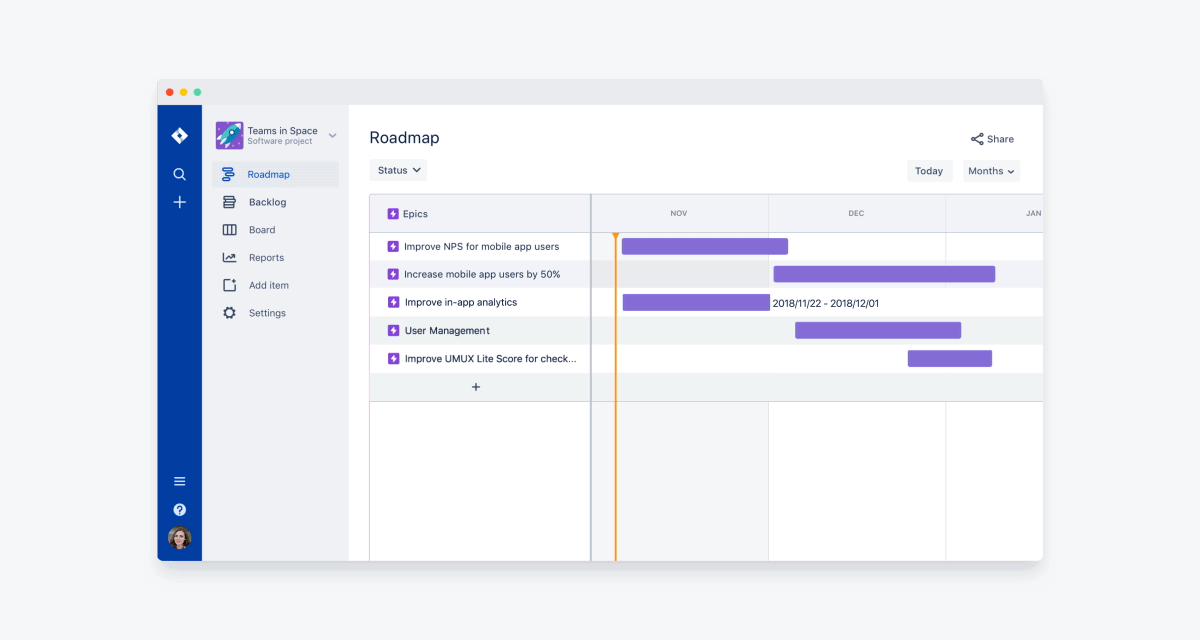
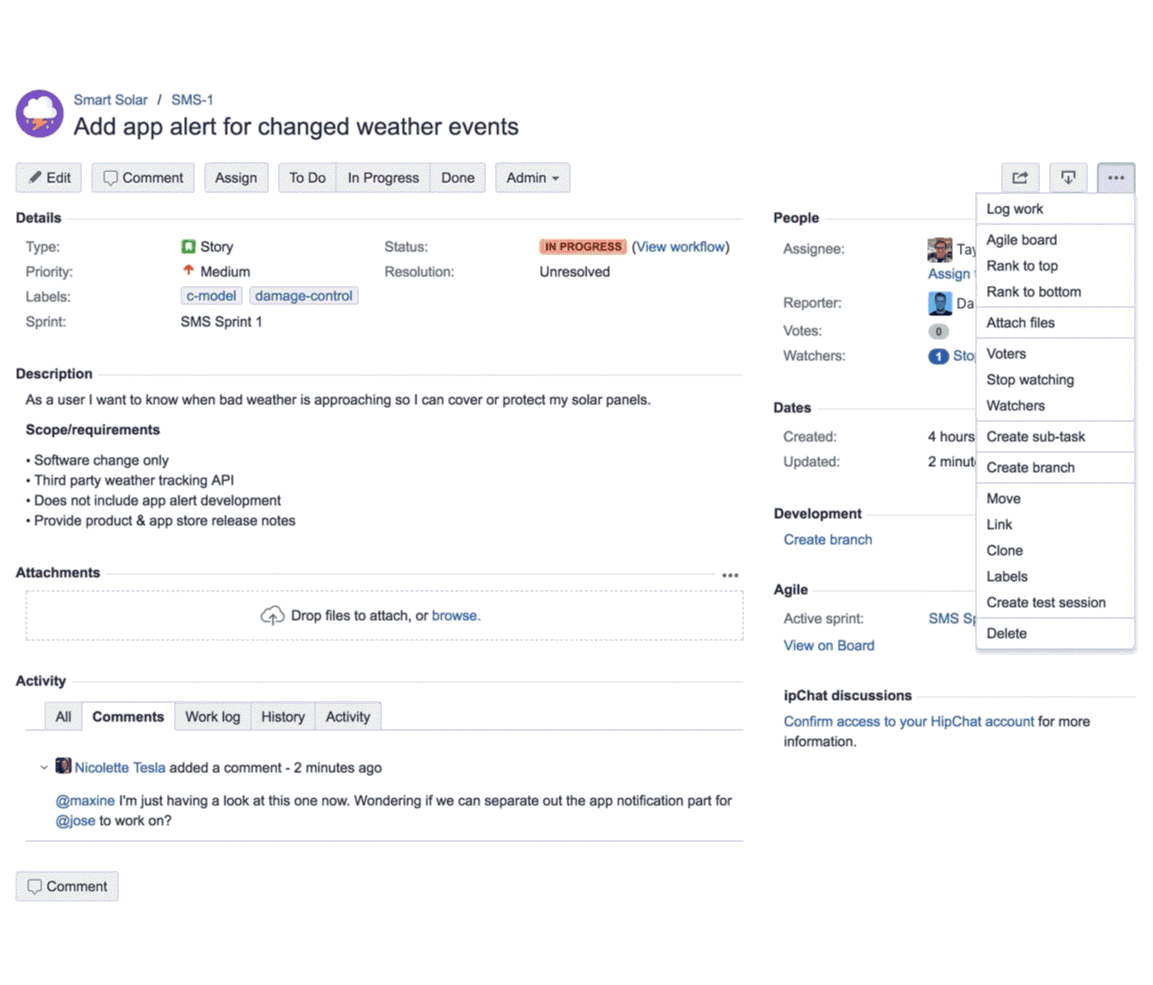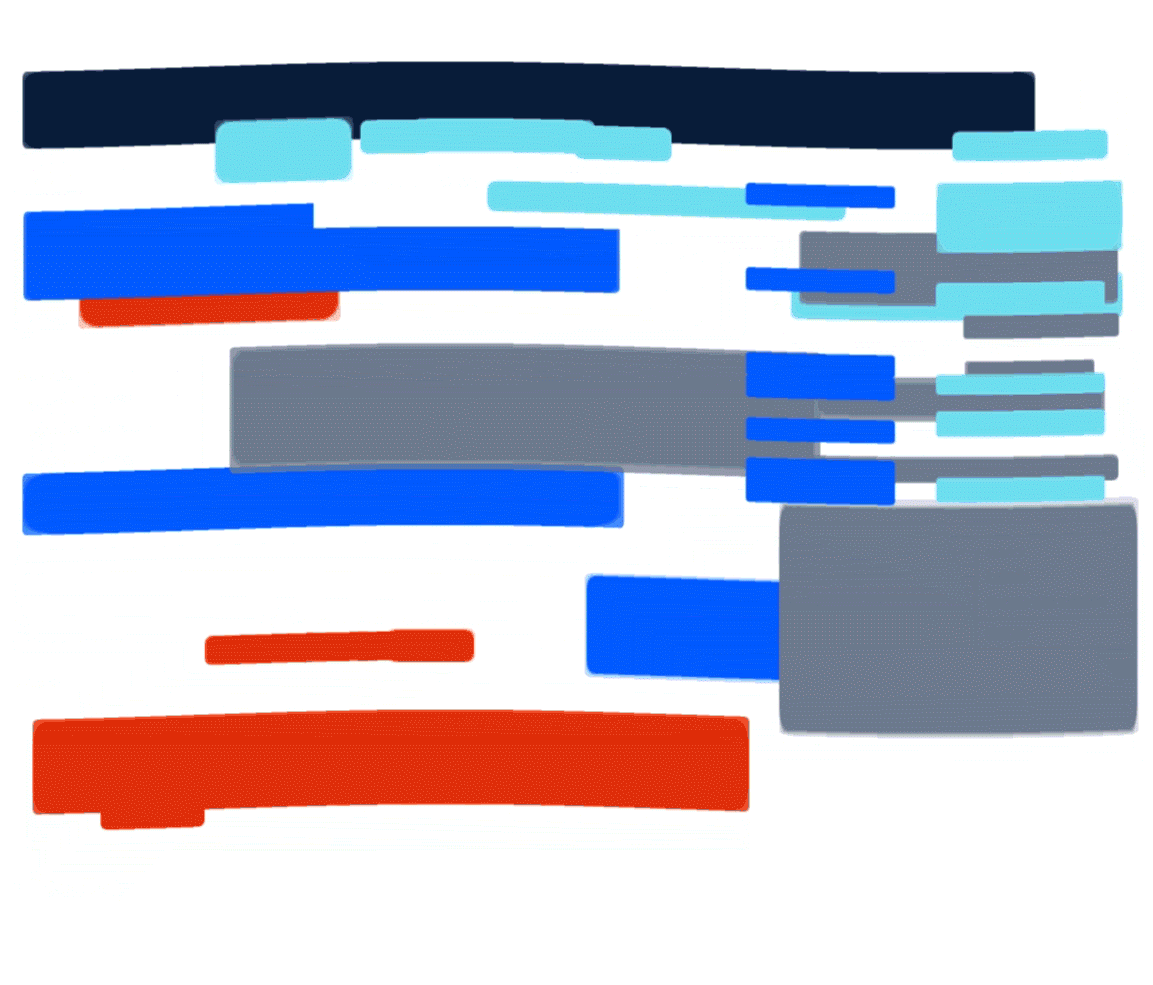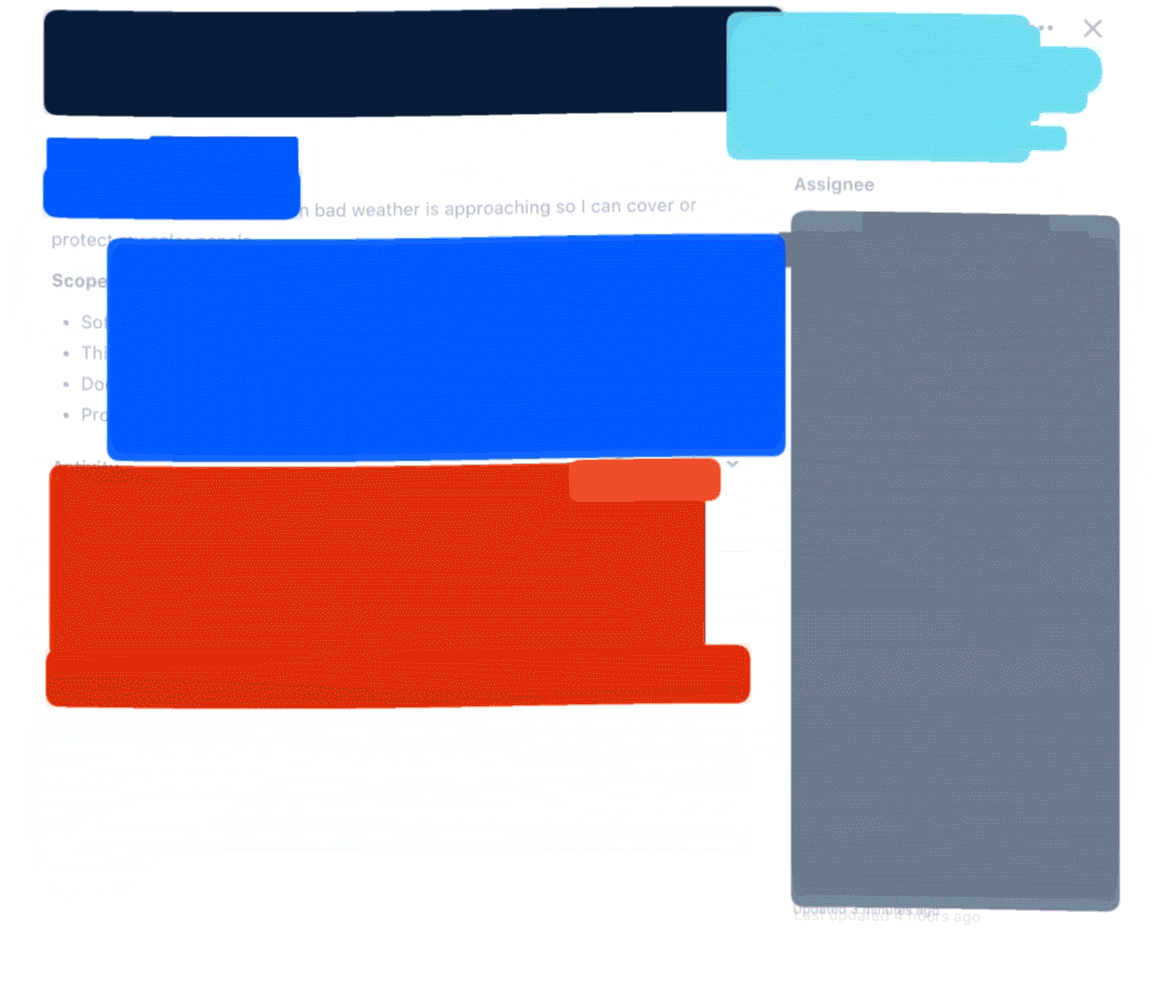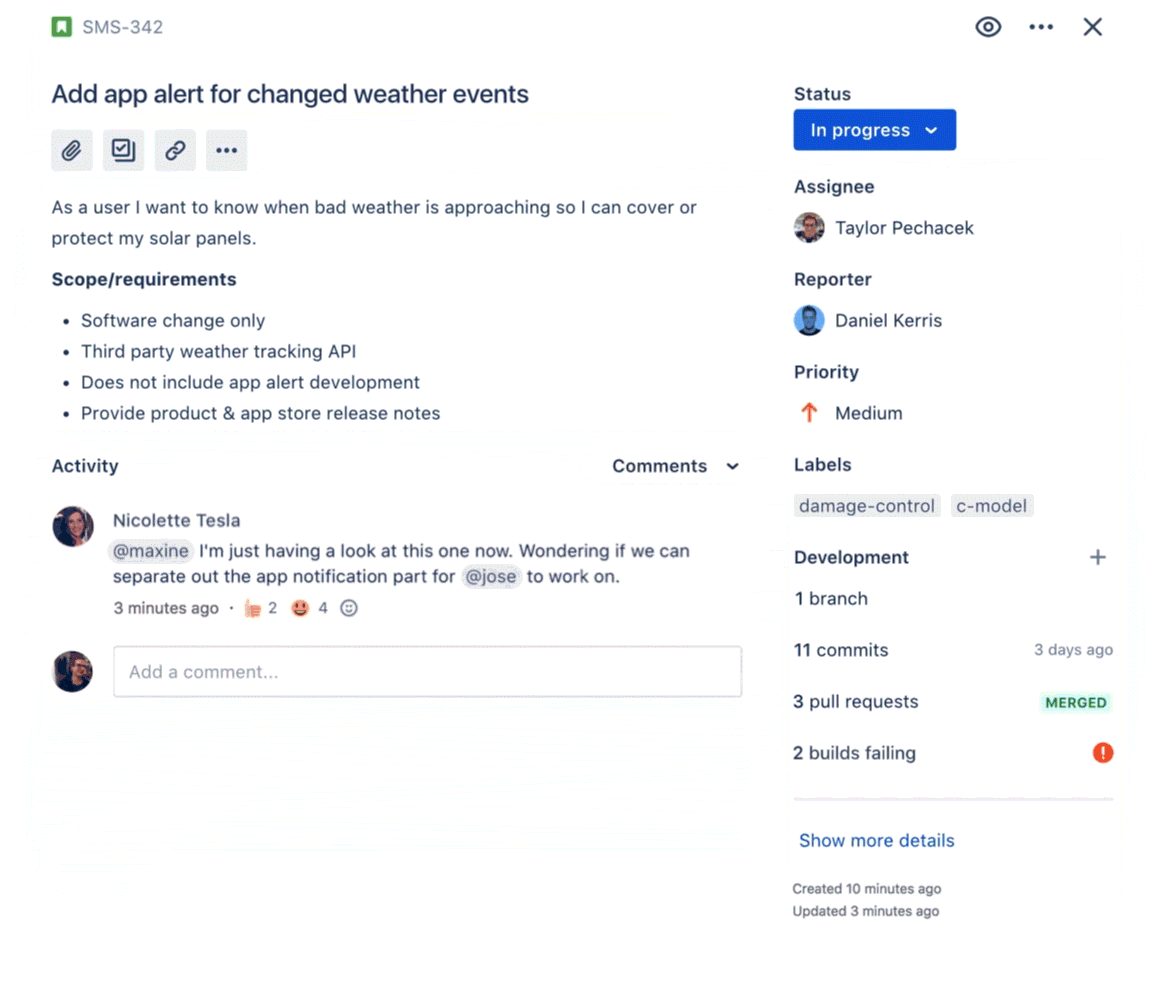
The System Preferences app in macOS offers quite a few settings to customize your Mac. When those are not enough, you’d normally have to rustle up a few Terminal commands to make visual as well as functional changes.
But what if you aren’t keen on fiddling with the Terminal app? You can still make the required changes with the following point-and-click tools. These tools make many built-in macOS features easily accessible without text commands.
1. TinkerTool
TinkerTool enables a few macOS features by default. For example, it adds a Quit Finder option to the Finder menu and programs the Backspace key to go back one page in Safari.
You’ll find the settings organized in logical panes such as Dock, Safari, Desktop, iTunes, etc. It’s best to tackle these panes one at a time to keep track of the tweaks that you’re making.
Any changes you make with the app stay restricted to your user account. Unlike the other apps on this list, TinkerTool doesn’t ask you for admin credentials to modify settings.
Here’s a short list of some of the useful changes you can make with TinkerTool:
- Insert separators in the Dock
- Change the default save location of Mac screenshots and their format too
- Enable single application mode, which hides all background apps when you switch to a new app
- Change the number of entries that show up in Recent Items menus
Worried about messing up crucial macOS settings with TinkerTool and having no way of going back? Rest assured that you can revert all the changes you make with the app and restore settings to their original state. All it takes is a click of the Reset to pre-TinkerTool state button on the Reset pane of the app.
Here, you’ll also find a Reset to defaults button in case you want to start using TinkerTool with a clean slate.
Download: TinkerTool (Free)
2. Onyx
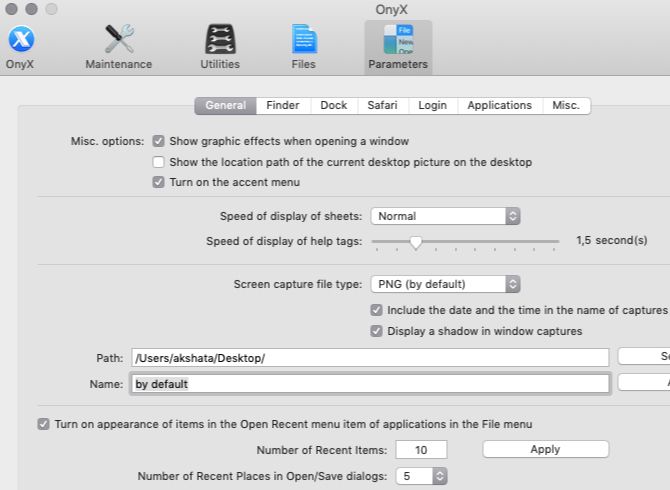
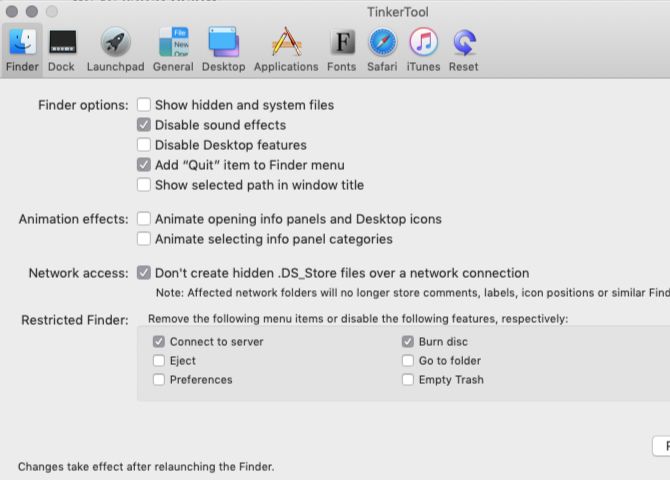
Onyx is part maintenance app and part tinkering tool. It can help you detect and fix common macOS problems and improve macOS with visual and functional changes. Let’s focus on the tinkering part for now.
Accordingly, the Parameters pane of Onyx is all that concerns us. Here, you’ll find quite a few settings listed under various categories like Finder, Dock, Login, and Safari.
Using these settings, you can, for example:
- Hide or display various Finder menu items
- Enable half-star ratings in iTunes
- Add a System Preferences pane for the built-in Archive Utility
- Configure screen capture functions
The developers of Onyx have a couple of other apps to handle the maintenance and personalization features of Onyx. They’re called Maintenance and Deeper respectively.
Maintenance gives you tools for tasks like cleaning system caches and running scripts. Deeper lets you customize hidden macOS functions, much like the Parameters pane of Onyx does.
However, Maintenance and Deeper haven’t been updated to work on macOS Mojave yet. The developers strictly advise against using non-compatible versions of these apps. So be sure to keep an eye out for their Mojave-compatible versions.
Download: Onyx (Free)
3. MacPilot
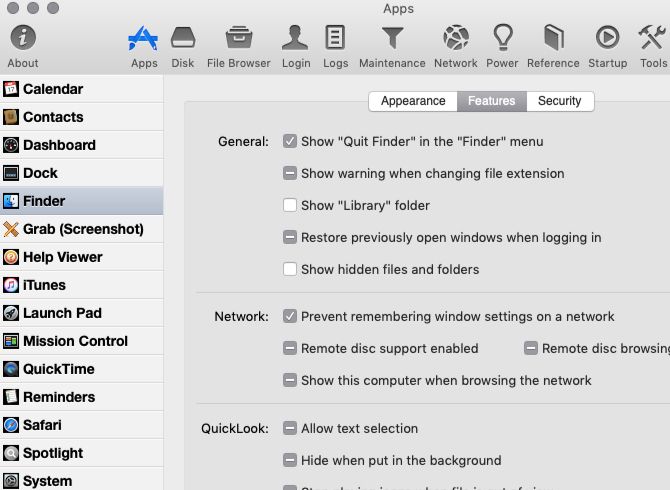
If you want granular control over your Mac’s features, MacPilot can hand it over to you. You can do a lot with this app!
For starters, you can:
- Add spacers to the Dock
- Configure Dock auto-hide delay
- Disable Notification Center and Mission Control
- Disable all animations
- Add a Quit Finder option to the Finder menu
- Change the format and location of macOS screenshots
- Erase files securely
- Force a specific display resolution
That’s a fraction of what you can do with MacPilot. No wonder the app comes across as a bit overwhelming—it lists so many settings.
It’s useful that MacPilot is well organized. You’ll find the major categories divided into panes; each pane further has nested categories that appear as a sidebar menu.
We recommend that you take your time going through each settings pane instead of making changes at random. It’ll help you avoid unnecessary confusion. Also, when in doubt about a setting, leave it alone until you research it well and know what you’re doing.
Even without its system maintenance features, MacPilot is worth paying for. Since it comes with a “try before you buy” policy, why not give it a shot?
Download: MacPilot ($30, free trial available)
4. Cocktail
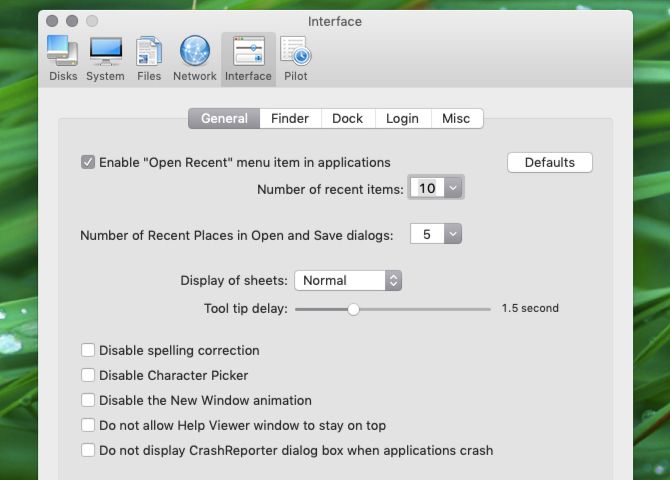
Like Onyx and MacPilot above, Cocktail has maintenance and personalization tools bundled into one app. Its Interface pane holds the settings you need to tweak elements in Finder, Dock, the login screen, and more.
Cocktail lets you disable window zooming, display the full folder path in the window title, and lock Dock icons and their sizes. Plus, you can configure Finder menu items, disable various animations, and enable half-star ratings in iTunes.
The app also allows you to prevent the Photos app from opening automatically when you connect a device. By the way, you can also do this using your Mac’s Image Capture app.
Pick Cocktail only if you’re planning to use its system maintenance features also. Otherwise, it’ll prove to be a costly purchase.
Download: Cocktail ($30, demo mode available)
Don’t Want to Use the Terminal? Ignore It
The apps above allow you to make many useful changes without disabling SIP (System Integrity Protection). Of course, with SIP enabled, you lose the ability to make certain advanced tweaks. You can still go ahead with them by disabling SIP (but we don’t recommend it)
What Is SIP? macOS System Integrity Protection Explained
What Is SIP? macOS System Integrity Protection Explained
What is System Integrity Protection on your Mac? We explain what SIP does and how it affects macOS software.
Read More
.
via MakeUseOf.com
4 Utilities for Tweaking Your Mac Without the Terminal