I’m asked about which code editor theme I use frequently enough to the point of being comical….Laracasts
Comic for August 09, 2021
https://assets.amuniversal.com/c9857e20d05601396d8e005056a9545d
Thank you for voting.
Hmm. Something went wrong. We will take a look as soon as we can.
Dilbert Daily Strip
The Miculek Magnetic Buffer System for AR-15 Rifles
https://cdn0.thetruthaboutguns.com/wp-content/uploads/2021/08/IMG_0578-scaled.jpg
Why would anyone spend money to reduce the recoil of an AR-15 rifle? That’s the question some will ask given the fact that a .223/5.56 round doesn’t produce a whole lotta recoil. Fair enough. For most shooters, it won’t make enough of a difference to matter. But if you’re a competitive shooter or are just sensitive to recoil, a recoil-reducing buffer makes sense.
The Miculek Magnetic Buffer System isn’t the first recoil reducer. Buffers using springs or hydraulics have been around for years. But the Miculek is a unique design using magnetic polarity to dampen the recoil impulse.
That means there are no moving parts to make noise or fail. With no springs or hydraulic seals, the Miculek Magnetic Buffer System (MMBS from now on) is damn near foolproof.
When you’re not using it in your rifle, the MMBS can double as a handy fridge magnet. But seriously folks . . .
Here you see the MMBS next to a standard M4 buffer. There are a couple of difference besides the recoil-reducing piston action. First, the MMBS weighs a tad more…3.2 oz versus 2.9 oz according to my kitchen scale. Also, the MMBS doesn’t rattle when you shake it like the standard buffer does.
I talked to the folks at JDAS enterprises who produce the MMBS with Jerry Miculek. They make the comps for Jerry, too, and tell me more Miculek designs are coming in the future.
JDAS said they’ve tested the buffer under more that 100,000 rounds without failure. They hooked it up to an accelerometer to objectively measure recoil and tested it for barrel deflection to see what it does for muzzle rise.
They told me that the MMBS is a significant improvement over a standard buffer and measurably better than either sprung or hydraulic designs.
Since I don’t have access to any of that equipment, the only way to tell if the MMBS does what they say it does is to shoot it.
Installing it takes all of 30 seconds. Just depress the buffer retention pin in your rifle’s lower — be sure to have your thumb over the sprung buffer or it will launch — and remove your standard buffer and spring. Slide the old buffer out of the recoil spring and install the MMBS. Reinstall it in your lower and you’re ready to go.
The strength of the dampening action of the MMBS is selectable with a screw that adjusts how much force is needed to depress the magnetic piston. The farther in your adjust the screw, the more force it takes to compress it. That lets you can tune your rifle as needed.
JDAS recommends tuning with a single round in a magazine. Shoot your rifle and if the action doesn’t lock back on the empty magazine, adjust the buffer with a counter-clockwise half-turn of the adjustment screw to lighten the tension. I didn’t have to do that as my rifle cycled just fine with the MMBS right out of the box.
First I shot two rifles side by side, one with a standard buffer and one with the MMBS. The rifle with the MMBS was slightly softer-shooting than the standard buffer. But while I was shooting the same ammo from each gun, the two rifles weren’t the same (different accessories, different weights, different muzzle devices. It wasn’t really a fair comparison.
Next I shot both with the same rifle, alternating between the two buffers. That’s a little tricky because you have to take the rifle down to replace the buffers between magazines. Still, there is a perceptible reduction in felt recoil when using the MMBS. It’s not a lot and it probably won’t make much of a difference to some shooters. But it’s there.
The MMBS has an MSRP of $119 and sells for $99 retail exclusively through Big Daddy Unlimited. That makes it less expensive than hydraulic buffers. Will it be worth it for you? That depends on how you shoot and how recoil sensitive you are. But if you want to do everything you can to reduce as much of the felt recoil your AR-15 rifle produces, the MMBS is well worth a try.
Post Views:
2
The Truth About Guns
Have You Ever Wondered How Americans And Brits Think They Would Do In Unarmed Combat Against Various Animals? Me Neither, But Luckily I Found This Graph.
https://media.notthebee.com/articles/3cf2a881-1b7e-4d53-8558-4b4727236b0f.jpg
Today while browsing the web, expecting to find more bad news, I stumbled across this graph that certainly brightened my day.
Not the Bee
The Best (Free) CAD Software for Mac
https://static1.makeuseofimages.com/wordpress/wp-content/uploads/2021/07/3D-Perspective-Design-Study-Room.jpg
Used by designers the world over, CAD, or computer-aided design and drafting (CADD), is design and documentation technology that replaces manual drafting (like blueprints, for example) with an automated process.
From architects and engineers through to audiovisual professionals and fashion houses, experts the world over use 2D and 3D CAD programs to draw up visual concepts, create construction documentation, and simulate designs in the real world through realistic renderings of a particular subject matter.
If you’re already a designer, or want to start getting into 2D and 3D design, there is a huge range of software out there that can be used for this purpose. In this article, we’ll explore eight free Mac applications, so you can get stuck into it sooner, and investigate which one rules the roost.
Most of these apps are free, but we are going to start with a paid, but reasonably priced option.
1. Leopoly

Promising to create new opportunities in 3D printing through fully customizable digital landscapes and 3D modeling, Leopoly is built for both newbies and more advanced users.
Its baseline ShapeLab tool enables users to become creators in minutes, building bespoke models and bringing your vision to life through digital sculpting, painting, and mesh-based technology. Going further, LeoTrainer enables full exploration of intricate processes and models—hence the name—where the training is oriented towards corporate and education worlds to familiarize users with concepts in virtual reality.
Finally, LeoShape is best suited to healthcare, fashion, and heavy-duty industries, promising enhanced modeling capabilities for those training or working in design; a great option for professionals.
Download: Leopoly ($20)
2. LibreCAD
In terms of a great beginner’s 2D program, LibreCAD‘s software can help you to create complex drawings, 2D drafts, or projects for laser cutting or engraving purposes. The tool comes with features like a snap-in tool, dimensioning and measurements, and annotations—a bit like a graphics editor such as Microsoft Paint, but with more intricacies.
It’s open-source and available for Mac, Windows, and Linux, and with no subscriptions, licensing costs, or annual fees, it could be the program for you.
Download: LibreCAD (Free)
3. LeoCAD

LeoCAD is probably the best CAD software for educational purposes, as it allows users to create virtual designs, shapes, and models using LEGOs, which is ideal for kids who want to get a head start with 3D modeling. With a combination of basic and advanced tools, its open-source nature means that anyone and everyone can contribute, and even add new features.
Download: LeoCAD (Free)
4. Blender
Blender has emerged as one of the best, most versatile CAD programs in the world in recent years. While it is very complex in nature, the possibilities are virtually endless with Blender. Open-source and completely free, its creation suite "supports the entirety of the 3D pipeline—modeling, rigging, animation, simulation, rendering, compositing and motion tracking, video editing, and 2D animation pipeline." Quite frankly, it’s a jack-of-all-trades for everything and everything 2D or 3D.
Users have been enthusiastic about the wide range of possibilities with Blender, and if you’re looking for a more advanced program to help you develop your CAD skills, this might be the one!
Download: Blender (Free)
5. DesignSpark

With an interface that is clearly borrowing from AutoCAD—the "industry-standard" for CAD design software—DesignSpark contains the usual features and is an excellent free alternative to AutoCAD. Users of programs like this would normally be attempting large-scale or intricate builds, like homes for example.
While core features are free, functions like bulk importing and exporting, and advanced rendering, need to be purchased, so that is a limitation. Interestingly, DesignSpark allows you to have designs printed in-house, and sent to you wherever you are.
Download: DesignSpark (Free, additional purchases available)
Related: The Best Home Design Software to Use
6. Houdini
Breaking from the other applications above, Houdini is procedural software that is designed around a node-based workflow. Similar to parametric modeling—which is what Blender uses, this allows you to alter models and objects by changing individual parameters or nodes. Similarly again to Blender, it includes intricate particle effects, which would allow users to create anything from an Alaskan winter terrain to a mock up of interstellar space. For this reason, it is also a popular tool for animation and game development.
Although a free version of Houdini (Apprentice) is available with all the same features as the freemium product, it has some limitations, such as a render size of just 1280×720 pixels, and every rendered image will feature a small Houdini logo.
Download: Houdini (Free, premium version available)
7. FreeCAD

While FreeCAD appears unassuming in name, it is a robust piece of software made to design real-life objects in 3D. Again utilizing parametric modeling, you can easily modify 3D designs and tailor them to a variety of settings or environments. It is modular in nature, allowing plugins to be attached to the application, and also offers handy features oriented towards robotics and mechanical machining like CNC.
It’s open-source and extremely powerful, so pace yourself in terms of becoming familiar with the program. Digging deeper will unleash a universe’s worth of potential for CAD enthusiasts.
Download: FreeCAD (Free)
There Are Lots of Free or Cheap CAD Apps for Mac
CAD software can help you design, create, and produce 2D and 3D objects, worlds, and more
This article has given you a small selection of free but powerful CAD applications, ranging from beginner ability to advanced users or professionals. For those looking to get into design, or build on their professional design skills, these apps could be perfect for you.
MUO – Feed
Comic for August 05, 2021
https://assets.amuniversal.com/2d51e000cd5c01396cf5005056a9545d
Thank you for voting.
Hmm. Something went wrong. We will take a look as soon as we can.
Dilbert Daily Strip
Pro-Vaxxer Encourages Mike Rowe to Push Vaccine on the Rest of Us. Mike Responds with Spicy PERFECTION!
https://www.louderwithcrowder.com/media-library/eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpbWFnZSI6Imh0dHBzOi8vYXNzZXRzLnJibC5tcy8yNzE0MzQ4MS9vcmlnaW4uanBnIiwiZXhwaXJlc19hdCI6MTYzMTY3MDYzMX0.3LksOvClMIP_Aqe7Iy3mGNAE2gWp8-4fYS94RaOOlh0/image.jpg?width=980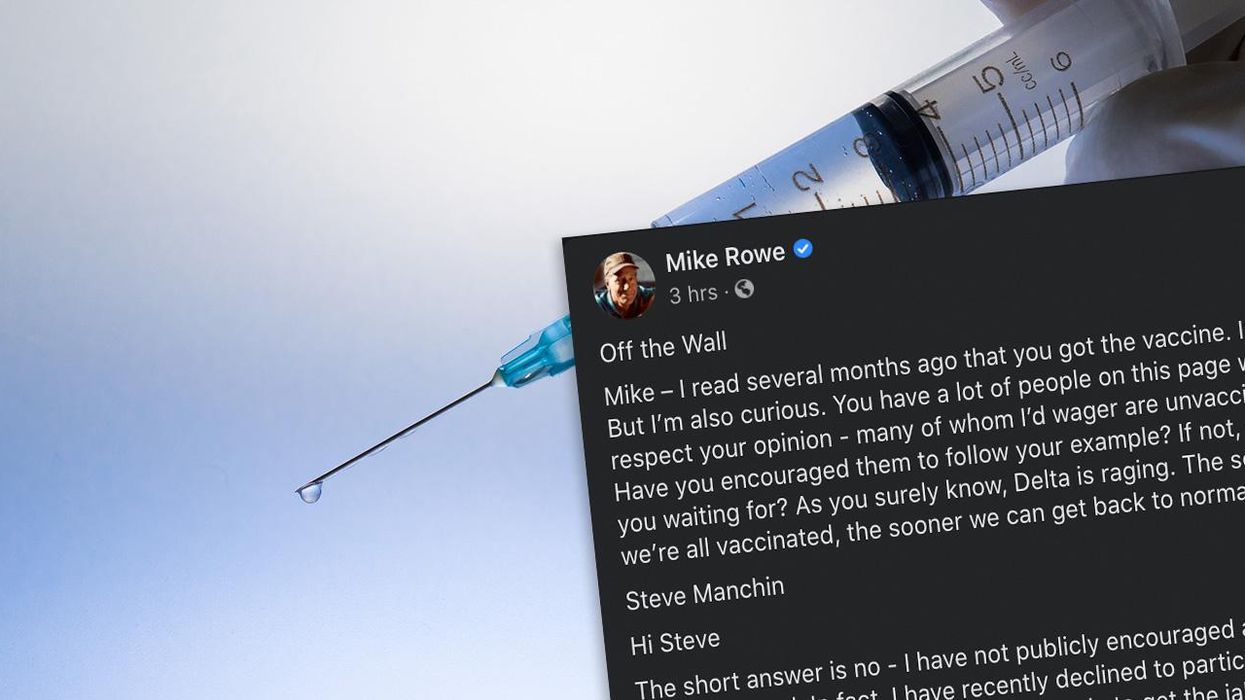
The Holy Vaccinated Saints are some of the most insufferable nimrods out there. I know we make fun of "Karens" but we need to expand and come up with some kind of denigrating moniker for the lot of them. One such pro-vaccine nimrod wrote into Mike Rowe, encouraging Mike to use the power of his influence to spread the Gospel according to Fauci. My words, "Steve" isn’t near clever enough to think up something half-way original. Not his fault, he was born a sheep. Anyway, Mike Rowe didn’t take the guilt bait, and instead of saying "no thanks, to each their own" he wrote a brilliant, spicy essay that every politico and their minions pushing the pokey should read and absorb. They won’t, but a girl can dream.
You’d need to click the "See More" link to read the full post, and you absolutely should, it’s Mike Rowe at his best. But a few of you might be on a social media hiatus or you, blessedly, told Facebook to go pound sand. I approve. If that be the case, here is my favorite chunk from Mike’s post:
"The fact is, millions of reasonable Americans have every right to feel confused and skeptical. Those people you refer to, Steve – the ones now telling us that we can "get back to normal just as soon as everyone is vaccinated" – those are the same people who said, "two weeks to flatten the curve!" Those are the same people who told us that masks were "useless" before they told us they were "critical." Those are the same people who told us that a return to normalcy would occur just as soon as "the most vulnerable" among us were vaccinated. Then, just as soon as "half the population" was vaccinated. Then, just as soon as we achieved "herd immunity." Those are the same people who told us they wouldn’t trust ANY vaccine developed under the last administration. Now, those very same people are belittling the skeptics!
If this were a Peanuts cartoon, those people would be Lucy, pulling away the football at the last moment while a nation full of Charlie Browns land flat on their collective back, over and over and over again. Those people you refer to – elected officials, journalists, and most disturbingly, more than a few medical experts – have moved the goalposts time and time again, while ignoring the same rules and restrictions they demand we all live by. They’re always certain, usually wrong, incapable of shame, and utterly void of humility. Is it any wonder millions find them unpersuasive?"
Mike is, as usual, right about this. A lot of us are skeptical. Speaking for myself, I cannot nor will I trust anyone in government to make my decisions. I make my decisions, and I make my own decisions better than an elected official and better than a butt-kissing sycophant who elected those assholes. I pride myself on critical thinking skills that I saw few people exercising at the start of the pandemic way back in February of 2020. What I did see was herd mentality in full swing. Plenty of right-leaning leaders went right along with it, too.
It’s good to be skeptical. It’s good to hit pause. Sometimes going with the herd is the right move. Sometimes it’s not. But that’s where thinking comes into play rather than just feeling and reacting to those feelings. Or in the case of much of the COVID panic, reacting to what others are feeling and saying so forcefully.
It’s your body and your choice. Remember that line? If you decide the vaccine is right for you, no one is stopping you. But some people have decided it’s not right for them. It isn’t up to you or anyone else to force them to do something they do not want to do to their body. Hard stop.
I have to add this last part, because it resonated with me:
At this point, I’m afraid the the government has but one course of sensible action – get the FDA on board, stat, and then, provide an honest, daily breakdown of just how quickly the virus is spreading among the unvaccinated, versus the vaccinated. No more threats, no more judgments, no more politics, no more celebrity-driven PSA’s, no more ham-fisted attempts at public shaming. Just a steady flow of verifiable data that definitively proves that the vast, undeniable, overwhelming majority of people who get this disease are unvaccinated. In other words, give us the facts, admit your mistakes, try on a bit of humility, and stop treating the unvaccinated like the enemy.
This is the gold: "no more ham-fisted attempts at public shaming" and "stop treating the unvaccinated like the enemy."
I’m tired of the vaccinated treating the unvaccinated like second class citizens. Or third class. Vermin, maybe. It’s gone on long enough and it’s gross. Hopefully those of us in the conservative crowd have been consistent in saying you need to do what you need to do, and so long as others are not negatively affected, fine. But man, the vaccinated people are teetering on the edge of becoming just as if not more obnoxious than the BAKE ME A CAKE, BIGOT Gaystapo soldiers.
Thanks for the wisdom, Mike. Hopefully it’ll resonate with the obnoxious vaccinated populace.
Get your content free from Big Tech’s filter. Bookmark this website and sign up for our newsletter!
Louder With Crowder
So This Is How The State Of Arkansas Is Promoting The Vaccine…
https://media.notthebee.com/articles/fd3a5afd-1553-4042-a2b2-289ebc8b8002.jpg
Love or hate the vax, this ad from the State of Arkansas will make you laugh out loud.
Not the Bee
The Best Metal Detector
https://cdn.thewirecutter.com/wp-content/media/2021/08/metaldetector-2048px-0377-3×2-1.jpg?auto=webp&quality=60&width=630&dpr=2

The dream of finding buried treasure is compelling, but the reality of metal detecting is that you mostly find trash—and you spend a lot of time doing it. This may be the sort of repetitive, mainly solitary activity you intrinsically enjoy … or it may bore you to tears. It’s best to figure that out before dropping a not-insignificant chunk of change on a metal detector of your own. So before you buy one, try to find a local club or store that will help you go on a trial hunt or two with an experienced detectorist. If the bug catches you, you’ll know it. And at that point, we’d say the Nokta Makro Simplex+ is the absolute best metal detector for a newcomer to the sport.
Wirecutter: Reviews for the Real World
Pioneering Paint App KidPix Is Back and Ready To Run in Your Browser
https://i.kinja-img.com/gawker-media/image/upload/c_fill,f_auto,fl_progressive,g_center,h_675,pg_1,q_80,w_1200/22224b3df903754d84557092af44bb96.png
Everything old is new again. In 2021, fanny packs are high fashion, Clippy is a beloved icon, and KidPix—the beloved art toy that’s been untouched since the early 2000’s—is back.
Well, sort of. Software engineer Vikrum Nijjar ported one of the original editions of KidPix into Javascript and HTML, turning the forgotten piece of software into something anyone can play with, right in their browser. While there have been many different editions of Pix released over the years, Nijjar’s port features the OG KidPix 1.0 that was released in 1989.
For the uninitiated, KidPix was kind of like baby’s first Photoshop. There were wacky paintbrushes, stamps, and drawing tools, along with other features that could allow you to add gradients, duplicate parts of your canvas, and more. The only snag is that none of these tools are actually labeled. Instead, the program is designed to let you learn what the tools do as you play around with them. Instead of an actual undo button, there’s the face of a shocked man who shouts “oops!” at you while undoing your work. If you want to clear your canvas entirely, you’ll need to find the firecracker button that—after playing an equally loud explosion—leaves you with a white page.
It is, in other words, very, very silly. But that’s what makes it so fun.
G/O Media may get a commission
After about ten minutes of clicking around and listening to the bizarre sounds some of the brushes made (the spirograph’s ‘weewoo’ was my personal favorite), I have to say this gets the 90’s kid seal of approval. It’s exactly the type of thing you want to play if you want to pretend, just for a second, to be sitting in your 1st-grade computer lab. Give it a try!
Gizmodo